BLOG
Healthcare SOC 2 FAQs
Published On January 18, 2022
Cyberattacks against healthcare organizations and their business associate vendors have begun to threaten patient safety and fundamental business operations. As a result, SOC 2 audit reports have become one of the most common and cost-effective vehicles for healthcare organizations to demonstrate adoption of controls relevant to security, availability, confidentiality, processing integrity and privacy.
Meditology Services is a top-ranked provider of information risk management, cybersecurity, privacy, and regulatory compliance consulting services, exclusively for healthcare organizations. Our Meditology Assurance division is an Association of International Certified Professional Accountants (AICPA) accredited provider of SOC 2 auditing, reporting, and attestations.
We have compiled these SOC 2 frequently asked questions to support healthcare organizations and vendors supporting the healthcare ecosystem that are looking to pursue SOC 2 examinations.
What is SOC 2 compliance?
Note: this section also addresses common questions including ‘What is a SOC 2 audit?’ and ‘What is a SOC 2 report?’.
According to the AICPA [1], System and Organization Controls (SOC) is a suite of service offerings CPAs may provide in connection with system-level controls of a service organization or entity-level controls of other organizations.
SOC reports are designed to help service organizations that provide services to other entities, build trust and confidence in the service performed and controls related to the services through a report by an independent CPA. Each type of SOC for Service Organizations report is designed to help service organizations meet specific user needs.
To be “SOC 2 compliant” typically means that an organization has obtained an independent assessment of controls that has been validated by an authorized third-party CPA firm and determined to have minimal or no deficiencies.
The most common SOC 2 report used by healthcare entities to demonstrate compliance with industry standard security controls is the SOC 2 Type II report. However, this is not the only SOC report and SOC audit available. The different types of SOC 2 reports are provided below.
What are the different types of SOC audits?
SOC 1 Audits
SOC 1 reports are defined by the AICPA as a Report on Controls at a Service Organization Relevant to User Entities’ Internal Control over Financial Reporting. [2]
These reports, prepared in accordance with AT-C section 320, Reporting on an Examination of Controls at a Service Organization Relevant to User Entities’ Internal Control Over Financial Reporting, are specifically intended to meet the needs of entities that use service organizations (user entities) and the CPAs that audit the user entities’ financial statements (user auditors), in evaluating the effect of the controls at the service organization on the user entities’ financial statements.
SOC 1 Type I
SOC 1 Type I is a report on the fairness of the presentation of management’s description of the service organization’s system and the suitability of the design of the controls to achieve the related control objectives included in the description as of a specified date.
In other words, SOC 1 Type I reports are issued for a point-in-time analysis of control implementation, but do not assess or audit controls over a longer period of time (see Type II for that objective).
SOC 1 Type II
SOC 1 Type II reports on the fairness of the presentation of management’s description of the service organization’s system and the suitability of the design and operating effectiveness of the controls to achieve the related control objectives included in the description throughout a specified period (e.g. 6 months).
In contrast to a SOC 1 Type I report, SOC 1 Type II audits assess controls over a period of time (e.g. six months, nine months, or one year). Type II reports provided a higher level of assurance of controls by inspecting implementation for a longer period of time.
SOC 2 Audits
SOC 2 reports are defined by the AICPA as a Report on Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality or Privacy. [3]
These reports are intended to meet the needs of a broad range of users that need detailed information and assurance about the controls at a service organization relevant to security, availability, confidentiality, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems. These reports can play an important role in:
- Oversight of the organization
- Vendor management programs
- Internal corporate governance and risk management processes
- Regulatory oversight
Similar to SOC 1 reports, SOC 2 reports also have two types: SOC 2 Type I and SOC 2 Type II.
SOC 2 Type I
SOC 2 Type I is a report on the fairness of the presentation of management’s description of the service organization’s system and the suitability of the design of the controls to achieve the related control objectives included in the description as of a specified date.
In other words, SOC 2 Type I reports are issued for a point-in-time analysis of control implementation, but do not assess or audit controls over a longer period of time (see SOC 2 Type II for that objective).
SOC 2 Type II
SOC 2 Type II reports on the fairness of the presentation of management’s description of the service organization’s system and the suitability of the design and operating effectiveness of the controls to achieve the related control objectives included in the description throughout a specified period (e.g. 6 months).
In contrast to a SOC 2 Type I report, SOC 2 Type II audits assess controls over a period of time (e.g. six months, nine months, or one year). Type II reports provided a higher level of assurance of controls by inspecting implementation for a longer period of time.
SOC 2 Type II is the most common SOC report used by healthcare entities to demonstrate compliance with industry standard security controls and trust principles.
Why do healthcare organizations obtain SOC 2 audit reports?
Third-party security assurance certifications and attestations including SOC 2 Type 2 reports have become a contractual requirement for third parties looking to do business with many of the nation’s leading healthcare organizations.
A top source of civil monetary penalties from OCR for HIPAA covered entities involves inadequate management and compliance for third-party business associates. In the case of an OCR audit, SOC 2 Type II reports help to demonstrate reasonable and appropriate compliance with regulatory requirements that apply to healthcare organizations.
SOC 2 examinations help vendors servicing healthcare companies to:
- Lessen the burden of risk assessments and questionnaire responses for customers
- Reduce sales cycle times
- Demonstrate compliance with industry standard security and risk models
- Limit the likelihood and impact of breach events, litigation, and regulatory scrutiny
SOC 2 examinations help healthcare entities to:
- Accelerate vendor risk assessment turnaround times
- Validate controls and gain assurance
- Save time, money, and resources by not having to validate controls with internal resources and teams
- Make informed supply chain risk decisions
- Scale vendor risk programs by relying on third-party assurance from SOC 2 attestations
Which healthcare organizations typically obtain SOC 2 audits?
Common categories of healthcare organizations that obtain SOC 2 reports include:
- Cloud hosting platforms
- Healthcare payers
- Data analytics firms
- Electronic Healthcare Records (EHR) solutions
- Healthcare vendors and business associates
- Research organizations
- Transcription companies
- Claims processing firms
- Healthcare consulting firms
- Leading healthcare providers
- Many more third parties servicing the healthcare industry
Are healthcare vendors required to obtain SOC 2 reports?
There is no regulatory requirement for healthcare organizations to obtain a SOC 2 audit or SOC 2 report. However, many healthcare organizations have begun to require vendors to maintain cybersecurity certifications like SOC 2 as a result of the increased volume and severity of cybersecurity risk exposures.
SOC 2 examinations provide assurance that vendors and other business associates are maintaining strong security and confidentiality controls and also serve as evidence that the healthcare entity has performed sufficient due diligence of vendors prior to permitting access to sensitive information and systems.
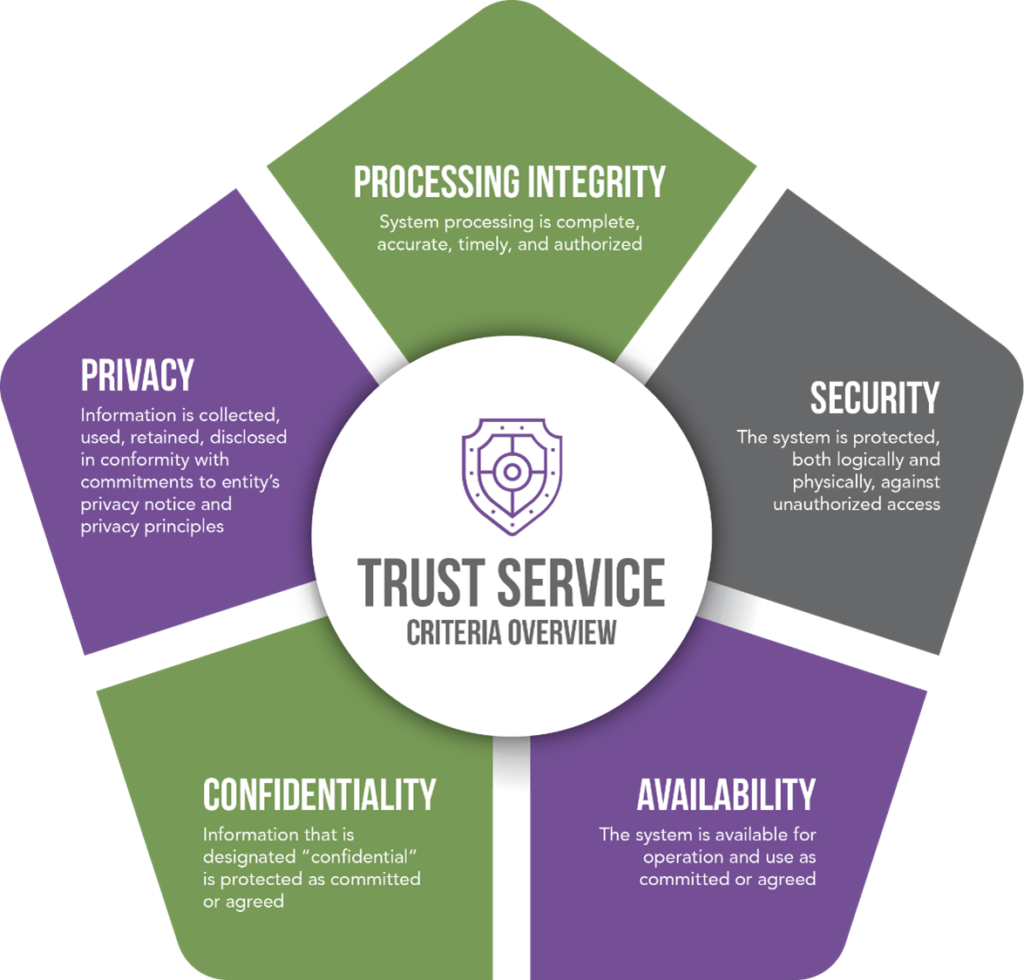
What are the AICPA Trust Criteria?
SOC 2 reports are specifically designed to report on the controls which make up the five AICPA Trust Criteria:
Security refers to the protection of information systems against unauthorized access or disclosure and preventing negative effects on systems which could affect the other trust principles. These controls include items such as physical and logical access controls.
Availability principle ensures that the information stored will be readily available to the authorized entity that requires it. These controls ensure that, if an event were to occur which brings the facility down, there are backups and protocols in place to restore service in a timely manner. This can also include preventative controls.
Confidentiality deals with controls which protect the confidentiality of data. This includes agreements and assessments with third parties regarding confidentiality.
Processing Integrity deals with making sure that system processing is complete, accurate, timely, and authorized.
Privacy ensures that information is collected, used, retained, disclosed in conformity with commitments to entity's privacy notice and privacy principles.
Most organizations attest to the criteria of Security, Availability and Confidentiality. Attesting to the Privacy and Processing Integrity criteria is much less common unless required by the service organization’s customer.
What other certifications are available for healthcare organizations?
The most adopted cybersecurity frameworks for healthcare organizations are SOC 2 Type II and HITRUST CSF certifications.
HITRUST offers several certification options:
- HITRUST bC: Basic Current State Assessment
- HITRUST i1: Implemented 1-Year Validated Assessment and Certification
- HITRUST r2: Risk-based 2-Year Validated Assessment and certification (Formerly the HITRUST CSF Validated Assessment)*
*The HITRUST r2, formerly called the CSF Validated Assessment, is the most adopted HITRUST certification.
The difference between these HITRUST assessment and certification options is the variance in level of effort and level of assurance that each assessment provides.
The HITRUST Basic Current State (bC) assessment provides a low level of assurance and requires a review of only 71 security controls. The HITRUST bC assessment is not a certification; the bC is a self-assessment only and does not require an external assessor firm to complete. Instead, it leverages the HITRUST Assurance Intelligence Engine to identify errors, omissions, or deceit, which is why HITRUST calls this a “Verified” Self-Assessment.
The HITRUST i1 certification, by contrast, provides a moderate level of assurance based on the NIST SP 800-171 controls framework and a subset of the HIPAA Security Rule. [2] The HITRUST i1 is good for one year only and organizations are evaluated against the implementation of controls only. The HITRUST i1 is a certifiable assessment and requires an external assessor firm like Meditology Services to complete. The level of effort to achieve the HITRUST i1 certification is substantially less than the HITRUST r2 certification and is reportedly more on par with the level of effort for a SOC 2 Type II attestation.
The HITRUST r2 certification provides a high level of assurance and requires a minimum review of 198 controls (up to 2000+ controls) to obtain certification. The HITRUST r2 certification is valid for a two-year period with an interim review required at the one-year mark. Organizations are evaluated on security policies, procedures, implementation, measurement, and managed practices. The HITRUST r2 certification includes a more comprehensive alignment with industry standards and regulatory requirements including the NIST Cybersecurity Framework and HIPAA (including the HIPAA Security Rule.)
Refer to the following resources to learn more about this topic:
- BLOG POST: HITRUST is Shaking Things Up: Details for the New HITRUST i1 Certification and bC Assessment
- PODCAST: HITRUST Announces New Certification Model: Insights from HITRUST Leadership
How does SOC 2 Type II compare to other certifications?
Obtaining enterprise cybersecurity certifications can be a daunting task for those embarking on the process for the first time, as well as those that are managing repeat certifications.
Some critical questions emerge: Which certification is the best for my organization? How do I limit the cost, time, and requirements to achieve certification? Will obtaining a healthcare certification make us HIPAA compliant? What else do I need to know to get through the certification process?
SOC 2 Type II reports and audits are typically less effort and cost than a HITRUST certification. However, HITRUST provides a more comprehensive assessment and higher degree of assurance than SOC 2 Type II.
SOC 2 Type II reports are not a certification. They provide a view into security controls that have been validated by qualified third-party assessors, however, the reports may note deficiencies or gaps against those controls. There is no pass or fail to a SOC 2 audit.
HITRUST provides a certification, meaning that organizations must obtain a passing score in order to receive a validated report (i.e. certification report). HITRUST also incorporates security control frameworks and regulations including HIPAA, NIST, PCI-DSS, state regulations, and more.
ISO certifications are occasionally adopted by vendors servicing healthcare organizations; however, ISO is more accepted and adopted for demonstration of security controls to international audiences.
Refer to the following resources to learn more about this topic:
- PODCAST: Are You Certifiable? Navigating Healthcare Security Certifications
- PODCAST: HITRUST Announces New Certification Model: Insights from HITRUST Leadership
What should my organization do to prepare for a SOC 2 audit?
It is highly recommended that organizations go through a readiness assessment prior to attempting to obtain a SOC 2 Type II audit report. Organizations should assess the requirements that will be in scope for when the certification time arrives.
SOC 2 readiness assessments allow the organization to prepare requisite documenting and evidence including policies, procedures, and configurations. It also allows the organization to build a working relationship with the AICPA-approved audit firm, which accelerates the SOC 2 audit process and reduces costs and effort when the time comes to go through the formal audit.
What is the SOC 2 reporting period?
The SOC 2 is a reporting framework intended to provide assurance that the in-scope controls are properly designed and operating effectively over a specified reporting period. This reporting period is typically 3 months long for the first SOC 2 audit and may be extended to 12 months thereafter.
How long does it take to complete a SOC 2 examination?
The duration of the audit and preparation activities is dependent upon the organization’s overall readiness and the defined reporting period. For organizations that are going through the SOC 2 Type II audit process for the first time, the process typically takes about one year to complete from start to finish. This can be accelerated under the right circumstances.
Organizations that have acquired SOC 2 audit reports for prior years can often complete the audit process in 3 to 6 months.
Who is qualified to perform a SOC 2 audit?
SOC 2 reports and audits must be performed by an accredited Certified Public Accountant or CPA firm. There are strict requirements for becoming a SOC auditing firm and maintaining that status including requirements to adhere to AICPA standards and undergo periodic peer review audits.
Organizations may choose to engage non-CPA firms to help prepare for SOC 2 audits; however, the formal audit and report by be conducted by an accredited CPA firm.
Meditology Services is leading provider of SOC 2 compliance services for the healthcare industry and is an accredited CPA firm authorized to conduct SOC 2 Type II examinations.
What are considerations for healthcare organizations when choosing a SOC 2 partner?
The selection of a SOC 2 partner and audit firm is a critical success factor for achieving a SOC 2 audit report with minimal deficiencies and reduced time and cost.
SOC 2 auditors must be an accredited Certified Public Accountant or CPA firm.
Experience in the healthcare industry is critical success factor for selecting a SOC 2 audit firm. Healthcare domain knowledge allows the audit firm to navigate your organization’s systems and controls efficiently and in alignment with industry standard implementations and controls.
What are Critical Success Factors for a Successful SOC 2 Engagement?
Critical success factors for obtaining SOC 2 reports include:
- Having the right stakeholders involved early on in the process
- Forming a governance committee and hold periodic status meetings
- Conducting a readiness assessment
- Reviewing the report for accuracy
- Performing periodic internal reviews
- Applying recommendations from SOC 2 audit readiness initiatives
What is the SOC 2 examination process?
A typical SOC 2 engagement includes three phases:
- Pre-audit preparation and readiness assessment
- Controls remediation
- Attestation audit
Pre-audit Preparation and Readiness Assessment
The readiness assessment process includes conducting pre-audit fieldwork which consists of a combination of interviews with key personnel, observation of users in the performance of their duties, and inspection of documents. Those results are then reported and include prioritized initiatives to close gaps against defined standards.
Controls Remediation
The controls remediation phase includes updating policies, procedures, and configurations to bring the organization into alignment and compliance with in-scope control requirements.
Attestation Audit
A formal audit is conducted for the defined audit period and in-scope controls and systems. The audit report is also developed which typically includes the auditor’s opinion regarding management’s written assertion regarding the organization’s description and compliance related to the AICPA/CICA Trust Services Criteria for Security for the in-scope environment.
Do the terms SOC 2 certification, SOC 2 attestation, and SOC 2 examination mean the same thing?
Yes. However, SOC 2 is technically not a certification but is better described as an attestation or examination.
How long is a SOC 2 audit report good for?
SOC 2 reports are valid for one year.
How often do SOC 2 examinations need to be renewed?
SOC 2 reports and attestations need to be renewed annually.
Can the SOC 2 report be shared outside my organization?
Yes, but the sharing of SOC 2 reports can only be authorized and initiated by your organization. The AICPA and CPA firms involved in the attestation process are prohibited from sharing the report or any related details publicly.
Can SOC 2 audits be conducted remotely?
Yes. The pandemic has driven entire workforces into remote operation at precisely the same time when the demand for independent inspection and validation of security controls for third-party vendors has reached peak levels.
These fundamental changes to business operations, systems, and controls require that SOC 2 audit approaches be revisited and adjusted to reflect new remote models and the risks they may introduce to organizations.
The AICPA released guidance titled FAQs - SOC 1® and SOC 2® Issues Arising From COVID‐19 [4] to help audit practitioners and businesses understand the impact of conducting remote SOC 2 audits in 2020 and beyond.
SOC 2 auditors often rely upon physical inspection and review of evidence to arrive at audit opinions outlined in SOC 2 attestations. The introduction of a remote workforce alongside limitations on travel and physical office and system inspections has the potential to hinder the effective collection and review of evidence of controls.
One option presented in the AICPA guidance is to consider delaying SOC 2 audits until such time as these conditions change. However, our experience working with our clients has shown that this course of action has proven impractical as the pandemic persists.
Another suggested tactic is to have remote workforce members capture and upload evidence of controls. This meets the requirements of the formal audit protocols; however, it can also introduce some inefficiencies in the evidence collection process. AICPA guidance also recommends that auditors maintain a “heightened sense of professional skepticism” for documentation submitted remotely vs. inspected in person.
Video conferencing technology including screen sharing capabilities has proven to be one of the more effective mechanisms for viewing and collecting controls evidence remotely. The agility of screen sharing allows auditors to work alongside the business representatives to navigate and observe multiple control areas without having to amass large volumes of static evidence.
Refer to the following resources to learn more about this topic:
- BLOG POST: SOC 2 Remote Audit Guidance
- AICPA GUIDANCE: FAQs - SOC 1® and SOC 2® Issues Arising From COVID‐19
What do Meditology’s SOC 2 compliance services include?
Meditology’s SOC 2 compliance services include:
- Providing formal attestation of SOC 2 security and privacy control requirements
- Assisting with the creation, design, and documentation of technical, physical, and procedural controls within your organization’s environment
- Identifying gaps within your environment’s control descriptions and associated processes
- Performing tests of Trust Services controls in advance of formal SOC 2 audits
- Assisting with the remediation of control gaps by ensuring existing controls are designed optimally, documented appropriately, and operating effectively
- Facilitating the exchange of control documentation and testing evidence during the execution of external SOC 2 audits
Can SOC 2 attestations be acquired using other security controls frameworks besides the trust principles?
Yes. The Trust Principles are the most commonly adopted control set used in SOC 2 attestations. However, it is possible to leverage other security controls frameworks such as the HITRUST CSF as the selected control set in scope for the SOC 2 attestation.
Is it possible to get a joint SOC 2 Type II and HITRUST CSF Certification?
Yes. Many organizations opt to obtain both HITRUST CSF Certification and SOC 2 reports simultaneously. Obtaining both certifications as part of one security initiative provides a cost-effective means of demonstrating effective security and privacy practices.
HITRUST demonstrates compliance with regulatory requirements that apply to healthcare organizations and provides a high-level of assurance to healthcare organizations.
While SOC 2 reports can be obtained by a wide range of industries, many of the security controls demonstrate compliance with HIPAA, which is an additional bonus for healthcare organizations and the businesses serving them.
Here are three ways in which a combination approach to HITRUST certification and SOC 2 attestation can benefit healthcare organizations:
- Compliance Readiness: First, these standards lay out a proven security assurance approach that works in healthcare settings. Healthcare organizations can improve their OCR compliance program readiness as the combination of these two security approaches covers much of the OCR focus areas. HITRUST was designed specifically for healthcare and SOC 2 provides an independent third-party opinion based on the AICPA’s Trust Services Criteria relating to its Information Technology controls.
- Resource Efficiency: Secondly, pursuing HITRUST certification and SOC 2 attestation in tandem provides resource efficiency as the HITRUST CSF requirements cover many of those within SOC 2 attestation. Pursuing these in the same project eliminates having to revisit one or both security programs in a separate project or audit. This frees up limited resources in the information security and technology areas for other high-priority projects. In addition, it meets third-party reporting needs and is an efficient and comprehensive reporting process.
- The Competitive Edge: Finally, businesses seeking to do business with healthcare clients may be asked to fill out security questionnaires. The security assurance task of filling out specific questionnaires and inquiries can be significantly reduced by the presence of a HITRUST CSF certification or SOC 2 attestation. Many times, providing proof that your organization has met the standards of HITRUST and SOC 2 is enough assurance to move a contract forward in the sales cycle.
Meditology is accredited to provide both SOC 2 and HITRUST certifications.
Refer to the following resources to learn more about this topic:
What Our Clients Are Saying“Value rating 5 out of 5, good value out of the partnership with Meditology because we could establish the relationship and I can call anyone on the team if I need advice. The Meditology team has helped us not only improve our business but become a distinguishing characteristic for us as a small business with a certification. We have been able to differentiate ourselves and there is value for our partners, they trust us.” - CISO, Data Analytics Organization |