
BLOG
PCI DSS v4.0 Released: Compliance Requirements for Healthcare Organizations
Published On April 6, 2022
The PCI Security Standards Council has released the much-anticipated PCI DSS version 4.0 this week. The update is several years in the making and includes significant control requirement overhauls.
Healthcare organizations must update policies, procedures, and control requirements to maintain compliance with the new PCI v4.0 standard. This blog post provides details about the new requirements for PCI v4.0 and the timing for compliance for healthcare entities.
What is New in PCI v4.0?
The PCI Security Standards Council has provided the following summary of major changes from PCI DSS v3.x to v4.0 [1]. The objectives of the changes implemented in version PCI v4.0 include:
- Adapting to New Threats – Organizations must continue to meet the security needs of the payments industry by evolving security practices as threats change. Examples of such adaptions in the new PCI 4.0 standard include expanded multi-factor authentication requirements, updated password requirements, and new e-commerce and phishing requirements.
- Promoting Security as a Continuous Process – According to the PCI Security Standards Council, “criminals never sleep; ongoing security is crucial to protect payment data.” Examples of continuous process adjustments include having clearly assigned roles and responsibilities for each requirement, guidance for implementation of controls, and new reporting options to highlight areas for corrective action.
- Increasing Flexibility – The PCI Security Standards Council has designed PCI v4.0 to support allowing different methods for organizations to achieve security objectives. Examples of flexible control implementation include the allowance of group and generic accounts, targeted risk analysis, and new methods to validate requirements.
- Enhanced Validation – PCI v4.0 includes new validation methods and procedures that are supported by the PCI Security Standards Council. This includes “alignment between information reported in a Report on Compliance or Self-Assessment Questionnaire and information summarized in an Attestation of Compliance.”
How Does PCI v4.0 Impact Healthcare Organizations?
Healthcare entities process credit card payments in a wide variety of settings that are often overlooked in information security and compliance program models. The new version 4.0 requirements need to be reflected by policies, procedures, and technical implementation for healthcare entities and their third -party payment card processing providers.
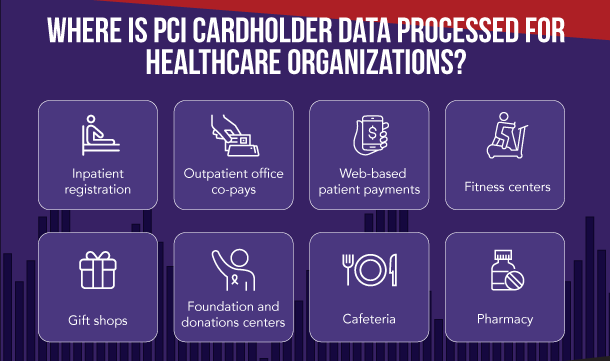 Image Source: Meditology Services, Healthcare Payment Card Compliance Risks
Image Source: Meditology Services, Healthcare Payment Card Compliance Risks
New PCI v4.0 control requirements will drive forward implementation of multi-factor authentication (MFA) for healthcare organizations. There are still some healthcare organizations that have not fully rolled out MFA across the enterprise including PCI systems and processes. MFA has wide-ranging protective benefits including helping to protect against ransomware attacks.
The latest evolution of MFA controls includes a requirement for confirming all multi-factor authentication factors before providing any indication of success or failure of a factor. This helps address risks related to automated password guessing attacks.
Requirements around password controls will also require healthcare entities to revisit their technical configurations and security tools for passwords. Specifically, the requirement to compare new passwords against a list of known, bad passwords.
Password length and complexity has been a hot-button topic the last few years following NIST’s release of guidance on same. Specifically, the requirement to compare new passwords against a list of known, bad passwords has been touted as a more reliable protection mechanism than only requiring very long and complex passwords.
Our experience has been that a combination of reasonable-length passwords (e.g. 10+ characters) plus preventing easily-guessable password creation is the optimal combination of controls. We believe including these requirements in the new PCI standard would go a long way toward broader adoption of these controls for the industry as a whole.
There are also provisions around authenticated vulnerability scans that will have impacts to specific control implementations for healthcare organizations.
Vulnerability scans can be conducted anonymously or using authenticated credentials (i.e. logged in with a valid username and password). Authenticated scans provide a much richer data set of vulnerabilities but can also be more time consuming and potentially disruptive to operations at times.
Unauthenticated or anonymous scans can more accurately simulate the vulnerabilities that would be visible to most external attackers. They are also more efficient to run and less likely to have an adverse impact on production systems. However, authenticated scans can provide more accurate insights into system vulnerabilities to detect and resolve issues that might otherwise go unnoticed.
Self-signed security certificates allow organizations to encrypt card holder data in transit (e.g. SSL and VPNs connections) without having to rely on a third-party certificate authority to issue the certifications. Using a self-signed certification would technically address the PCI requirements for encryption but could expose the organization to risk of compromised self-signed certs, which often are created without expiration.
Third-party certificate authorities are a cornerstone of the trust model that runs modern Internet-based transmission of sensitive data. In my view, the sensitivity of card holder data is too high to allow self-signed certificates to be used for any Internet-facing transmission use cases.
Other common challenges in healthcare for PCI compliance may also be exacerbated by a shift in control requirements including:
- Updated documentation of payment card processes and credit card environments
- Lack of network segmentation and needing to apply PCI controls across the entire environment
- Tracking and monitoring of access to payment card systems and data
- Security event monitoring across disparate environments
- Limited security capabilities of legacy systems and applications to meet the new standards
- Needing to update PCI contractual language for third party service providers
- Obtaining management support to perform remediation for new controls
- Lack of skillset or personnel that understand PCI DSS v4.0 and new requirements
What is the Timeline for Compliance with PCI v4.0?
The PCI Security Standards Council has released an overall implementation timeline that outlines the timing for organizations to transition from prior versions of the standard to the new PCI v4.0 standard.
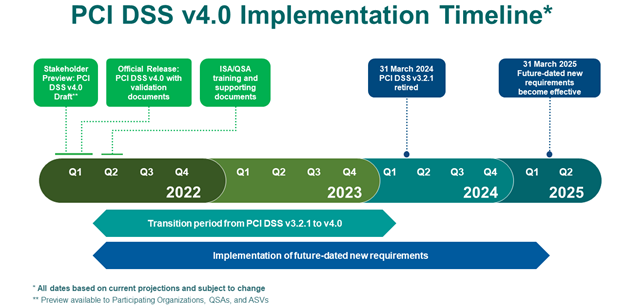 Image Source: PCI Security Standards Council, https://blog.pcisecuritystandards.org/countdown-to-pci-dss-v4.0
Image Source: PCI Security Standards Council, https://blog.pcisecuritystandards.org/countdown-to-pci-dss-v4.0
The PCI Security Standards Council has also defined a transition period which allows organizations to adjust to the new requirements that spans an 18-month time period. Some of the new requirements are also designated as “future-dated requirements”. This means that these requirements will not need to be in place for validation but should be considered as best practices until such time as the council designates them as required provisions.
An overview of the transition period timing is provided by the PCI Security Standards Council as follows:
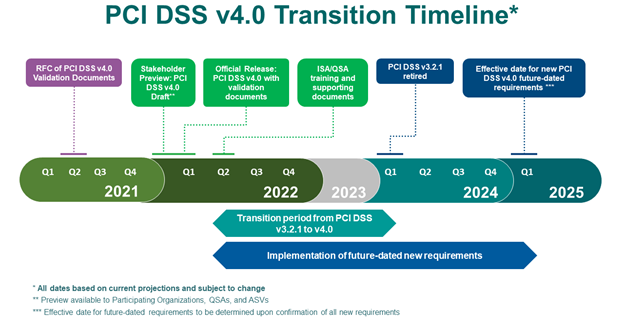 Image Source: PCI Security Standards Council, https://blog.pcisecuritystandards.org/updated-pci-dss-v4.0-timeline
Image Source: PCI Security Standards Council, https://blog.pcisecuritystandards.org/updated-pci-dss-v4.0-timeline
The full line-by-line control level changes are available from the PCI Council in the following document: Summary of Changes from PCI DSS Version 3.2.1 to 4.0.
Meditology is an accredited PCI DSS Qualified Security Assessor (QSA) and Approved Scanning Vendor (ASV) company that exclusively serves the healthcare industry.
Meditology’s PCI services for healthcare organizations include:
Contact us to learn more or to discuss your specific circumstances and plans for PCI-DSS adoption and compliance.
